This blogpost has a Interesting level of High
TL;DR: A childcare website is compromised and seems to be redirecting to a potentially malicious website. How much access does the attacker have?
Huge props to Anon for the find and collaborative research!
Intro
The following was written on 10-08-2022
During a “random” google images search Anon found the following image entry:
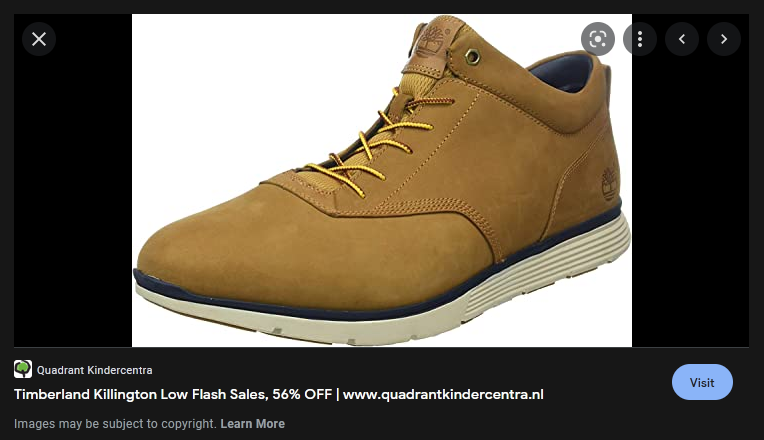
The image itself is not strange but the website that hosts it is not expected. The URL is:
https://www.quadrantkindercentra[.]nl/vacature_werknemers/werkenbijquadrant-yoeri/?w=3.557.3807013.5.23.84.timberland+killington+lowThis brings you on the following page on the domain (oypmall[.]com):
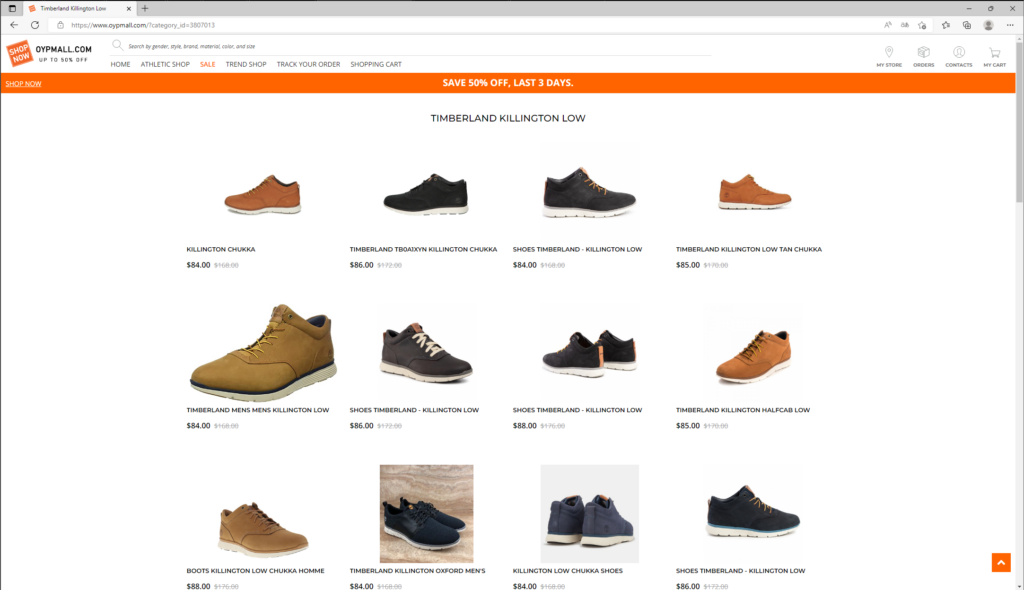
Okay why is a Childcare website redirecting me to a malicious looking webshop. This is strange…
And there is where the story starts!
Investigation
Under investigation is the website www.quadrantkindercentra[.]nl
This is a Dutch childcare group that is responsible for a huge amount of childcare locations around Gouda.
When looking into the domain where we are redirected to (oypmall[.]com) we can find the following info:
- Registered on 25-07-2022
- Registered on NameCheap
- Let’s Encrypt SSL certificate for
*.oypmall[.]com - Uses Cloudflare to mask its IP
- Registrant details are masked by NameCheap
Sources:
- https://www.virustotal.com/gui/
domain/oypmall.com/details - https://urlscan.io/result/848e3aa6-cda3-4b93-b350-54a93497120b/
On first sight this seems like a malicious webshop but this cannot be said for sure. The thing that makes it seem very malicious is the way it redirects from our root domain www.quadrantkindercentra[.]nl
URI breakdown
Let’s break down the URI, specifically the part after ?w=
/?w=3.557.3807013.5.23.84.timberland+killington+low- The first value (3) is called “a” in the cookie
- The second value (557) is called “b” in the cookie
- The third value (3807013) is called “c” in the cookie
- The fourth, fifth and sixth values do not seem to be stored in the cookie
- The text value changes the header text above the products
Changing the third value “c” changes the category ID on the website. The first and second value change the products shown but the further actions or reasoning is not known.
The reason for the redirection behaviour is not known exactly but it looks like a malicious script or plugin on the website is interpreting the specific URI and redirecting you.
Investigating the backend
What could have compromised this website to make it exhibit this strange behaviour?
With some digging the following interesting things can be found about this website:
- The website runs WordPress!
- WordPress is not recently updated (5.7.6, released on 2022-03-11)
- PHP 7.2.34 is installed
- The website uses a custom theme called “quadrant-kindercentra-todd-reclame”
- The website runs multiple plugins but these two are the most interesting because they are outdated and contain vulnerabilities:
- contact-form-7
- CVE-2020-35489 ~ Unrestricted File Upload
- Version details:
Installed v5.2
Vulnerability fixed in V5.3.2
Newest V5.6.3
- wordpress-seo
- CVE-2021-25118 ~ Unauthenticated Full Path Disclosure
- Version details:
Installed v14.6.1
Vulnerability introduced in V16.7
Vulnerability fixed in V17.3
Newest V19.6.1 - This vulnerability isn’t a threat because the website runs an even older version of this plugin 😉
- contact-form-7
- The website’s custom theme has a file named error_log hosted publicly
Deeper look at the custom theme
Let’s dig in! We begin at:
https://www.quadrantkindercentra[.]nl/wp-content/themes/quadrant-kindercentra-todd-reclame/readme.txtThis shows a readme with the following notable information:
Requires at least: 4.0
Tested up to: 4.2.2
Stable tag: 1.0.0
== Description ==
Hi. I'm a starter theme called QuadrantKindercentra V2, or underscores, if you like. I'm a theme meant for hacking so don't use me as a Parent Theme. Instead try turning me into the next, most awesome, WordPress theme out there. That's what I'm here for.
== Changelog ==
= 1.0 - May 12 2015 =
* Initial release
== Credits ==
* Based on Underscores http://underscores.me/, (C) 2012-2015 Automattic, Inc., [GPLv2 or later](https://www.gnu.org/licenses/gpl-2.0.html)This could indicate that this theme is made for WordPress 4.X and the theme was made/released on 12-05-2015 and hasn’t been updated since.
The theme seems to be based on a theme named Underscores which is found on -> GitHub: https://github.com/Automattic/_s
Let’s look at the error_log file:
https://www.quadrantkindercentra[.]nl/wp-content/themes/quadrant-kindercentra-todd-reclame/error_logThe contents are as follows:
[24-May-2016 12:19:08 Europe/Amsterdam] PHP Fatal error: Call to undefined function get_header() in /home/quadrcen/public_html/wp-content/themes/quadrant-kindercentra-todd-reclame/index.php on line 15
[24-May-2016 12:19:08 Europe/Amsterdam] PHP Fatal error: Call to undefined function get_header() in /home/quadrcen/public_html/wp-content/themes/quadrant-kindercentra-todd-reclame/index.php on line 15
[24-May-2016 12:19:08 Europe/Amsterdam] PHP Fatal error: Call to undefined function get_header() in /home/quadrcen/public_html/wp-content/themes/quadrant-kindercentra-todd-reclame/index.php on line 15
--------------------TRUNCATED------------------
[06-Aug-2016 14:41:20 Europe/Amsterdam] PHP Fatal error: Call to undefined function add_action() in /home/quadrcen/public_html/wp-content/themes/quadrant-kindercentra-todd-reclame/functions.php on line 81
[07-Aug-2016 18:01:48 Europe/Amsterdam] PHP Fatal error: Call to undefined function language_attributes() in /home/quadrcen/public_html/wp-content/themes/quadrant-kindercentra-todd-reclame/header.php on line 2
[07-Aug-2016 18:01:48 Europe/Amsterdam] PHP Fatal error: Call to undefined function wp_footer() in /home/quadrcen/public_html/wp-content/themes/quadrant-kindercentra-todd-reclame/footer.php on line 1
[07-Aug-2016 18:01:49 Europe/Amsterdam] PHP Fatal error: Call to undefined function get_header() in /home/quadrcen/public_html/wp-content/themes/quadrant-kindercentra-todd-reclame/404.php on line 3
[11-Aug-2016 07:12:27 Europe/Amsterdam] PHP Fatal error: Call to undefined function add_action() in /home/quadrcen/public_html/wp-content/themes/quadrant-kindercentra-todd-reclame/functions.php on line 81
--------------------TRUNCATED------------------
[27-Aug-2018 22:16:00 Europe/Amsterdam] PHP Fatal error: Call to undefined function get_header() in /home/quadrcen/public_html/wp-content/themes/quadrant-kindercentra-todd-reclame/archive.php on line 1
[27-Aug-2018 22:16:00 Europe/Amsterdam] PHP Fatal error: Call to undefined function get_header() in /home/quadrcen/public_html/wp-content/themes/quadrant-kindercentra-todd-reclame/index.php on line 15
[27-Aug-2018 22:16:01 Europe/Amsterdam] PHP Fatal error: Call to undefined function get_header() in /home/quadrcen/public_html/wp-content/themes/quadrant-kindercentra-todd-reclame/index.php on line 15The log file starts on 24-05-2016 and ends on 27-08-2018.
These kind of files should never be publicly accessible because this file possibly gives insight into the internal directory structure of this website and/or webserver.
contact-form-7 vulnerability
When checking for the contact-form-7 vulnerability we can see that the following is listed as the description:
CVE-2020-35489
The contact-form-7 (aka Contact Form 7) plugin before 5.3.2 for WordPress allows Unrestricted File Upload and remote code execution because a filename may contain special characters.
This could mean that if we can upload a file anywhere on this website we could use this vulnerability to possibly exploit this website.
And there is a place to upload files on this website:
https://www.quadrantkindercentra[.]nl/werkenbij/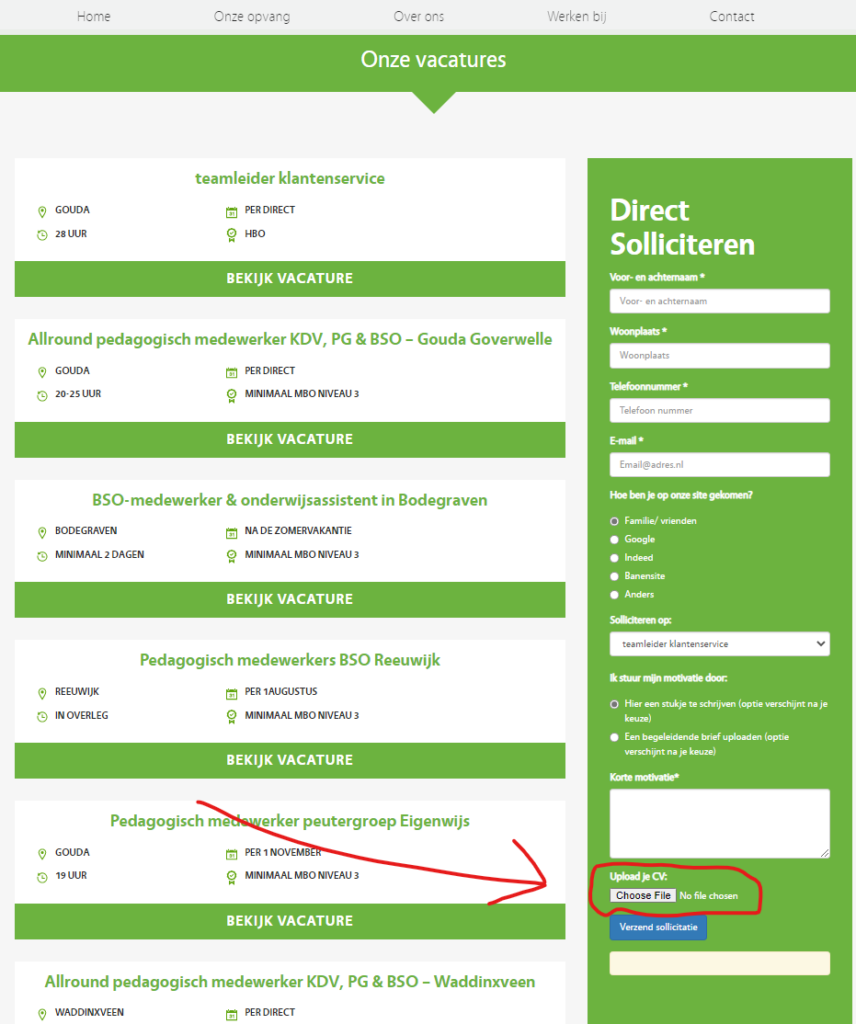
Bingo! Of course we won’t try to see if the exploit works, that would be crossing a line, but this could be the entryway for a possible attacker to have dropped the redirect script on the website.
Fun facts:
Funny thing is the website runs WordFence which is a plugin that acts as a Web Application Firewall and is a very populair WordPress plugin to secure your WordPress website. You can observe WordFence working by trying script kiddo tactics and entering a <script>alert('test');</script> in the searchbar or any other inputfield and you will get this:
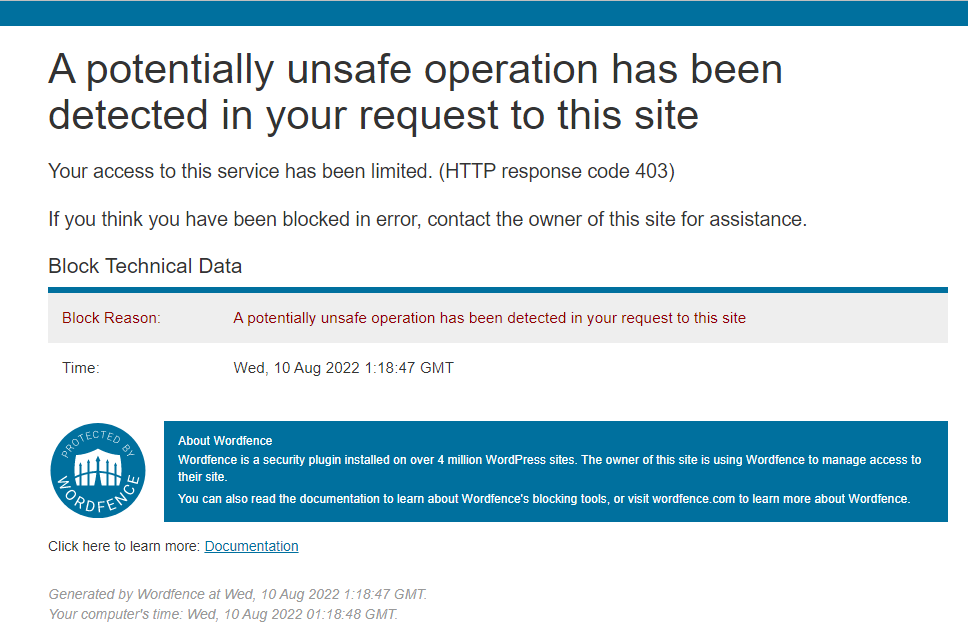
The website also seems to be indexing keywords from the redirected site on google:
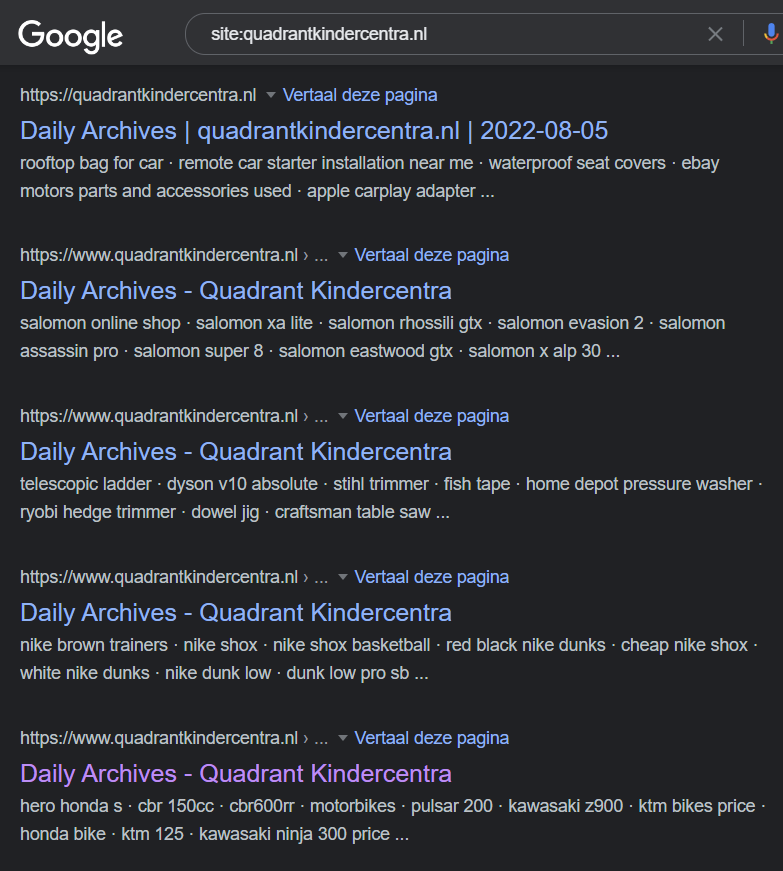
Conclusion
The website under investigation seems to be compromised. At the surface it appears to be a a simple sneaky redirect script? Why this is present, no idea.
But who knows how much access a possible attacker has to the backend of this WordPress site, and the data people have entered on it.
Therefore we will report this to the website owner ASAP so that they can verify these findings.
THIS BLOGPOST WILL NOT BE PUBLIC UNTIL WE HAVE WAITED AT LEAST 90 DAYS FOR A REPLY FROM THE WEBSITE OWNER
Also this was written on 10-8-2022 from ~02:00 until ~03:45 so spelling and grammatical error’s are expected, time for much needed sleep now!
Update 10-8-2022 (~16:00)
More about oypmall[.]com
When investigating the website some more we can observe that the website looks very sketch and is too good to be true. Lines such as:
- SAVE 50% OFF, LAST 3 DAYS.
- UP TO 50% OFF, Last 24 hour !
- Super savings!
Furthermore the following statements are observed with “Learn More” links:
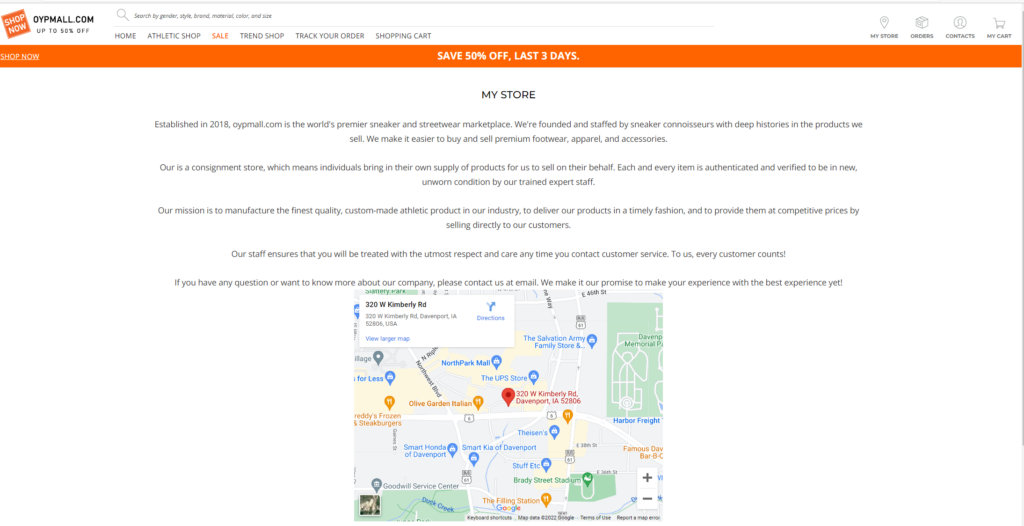
When going to the store locator you can see that there are no 500 locations to shop. Furthermore, the address listed is not of this store, but that of an unrelated store in the USA.
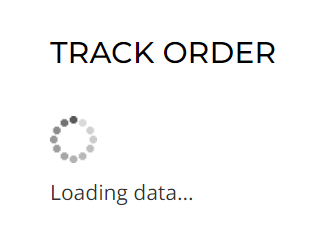
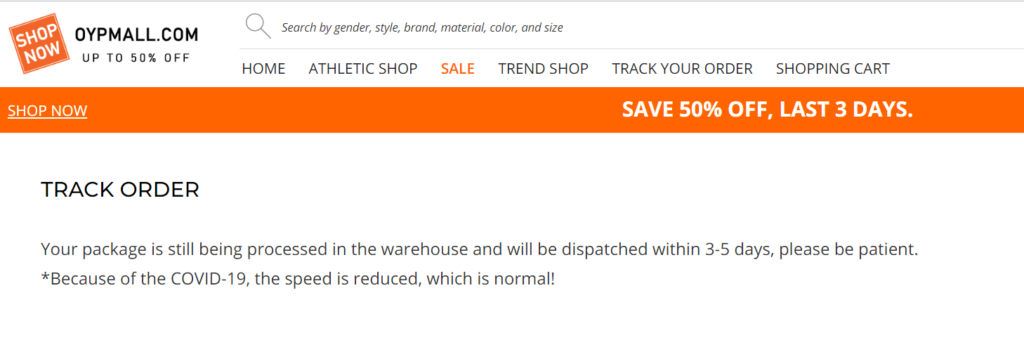
The track your order page is huge fun also:
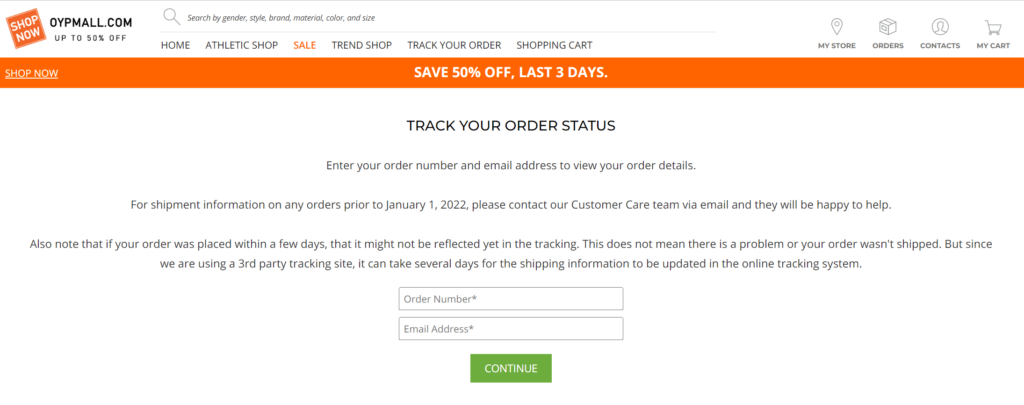
You can enter bogus details and it will give you the following message:
The contact us page lists the following email address for general “inquries”, yes that spelling mistake is on the website itself:
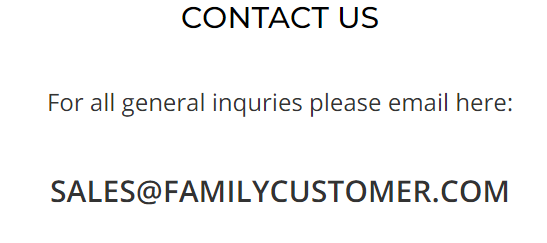
This is another red flag as this domain isn’t related to this domain but also the domain familycustomer[.]com does not resolve to a website at this time. But it is registered with whois protection, this means we cannot see who registered this domain.
The domain familycustomer[.]com does seem to have mx (mailserver) records set:
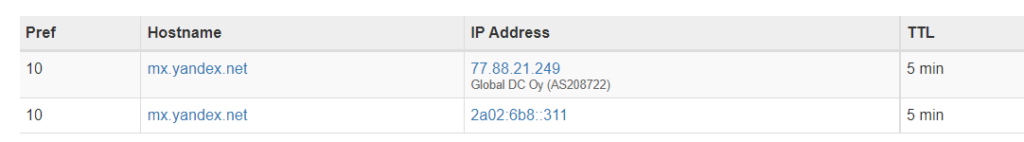
This could be linked to a potential Russian server and/or owner as Yandex is described as the following:
Yandex LLC is a Russian multinational technology company providing Internet-related products and services, including an Internet search engine, information services, e-commerce, transportation, maps and navigation, mobile applications, and online advertising.
Wikipedia
Multiple other links on the website do not seem to work. All points considered, we can say with certainty that this website is indeed malicious in nature.
Update 13-9-2022
No response and website is still compromised
Since reporting these findings, no response has been received and no changes to the website seem to have been made. The website still redirects to a web shop in similar style, but now under a different domain:
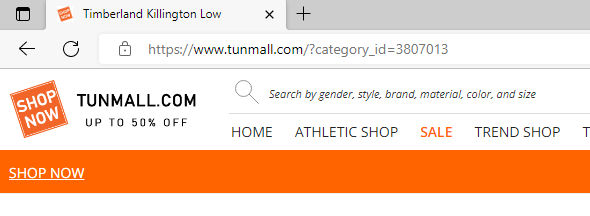
This domain has almost the same registrar information, it was only registered on a later date than the other domain:
- Registered on 24-08-2022
- Registered on NameCheap
- Let’s Encrypt SSL certificate for
*.tunmall[.]com - Uses Cloudflare to mask its IP
- Registrant details are masked by NameCheap:
Registry Registrant ID:
Registrant Name: Redacted for Privacy
Registrant Organization: Privacy service provided by Withheld for Privacy ehf
Registrant Street: Kalkofnsvegur 2
Registrant City: Reykjavik
Registrant State/Province: Capital Region
Registrant Postal Code: 101
Registrant Country: IS
Registrant Phone: +354.4212434Recently, more vulnerabilities for WordPress have been discovered. As stated before, this server is still running version 5.7.6 and the following vulnerabilities have been fixed in 5.7.7:
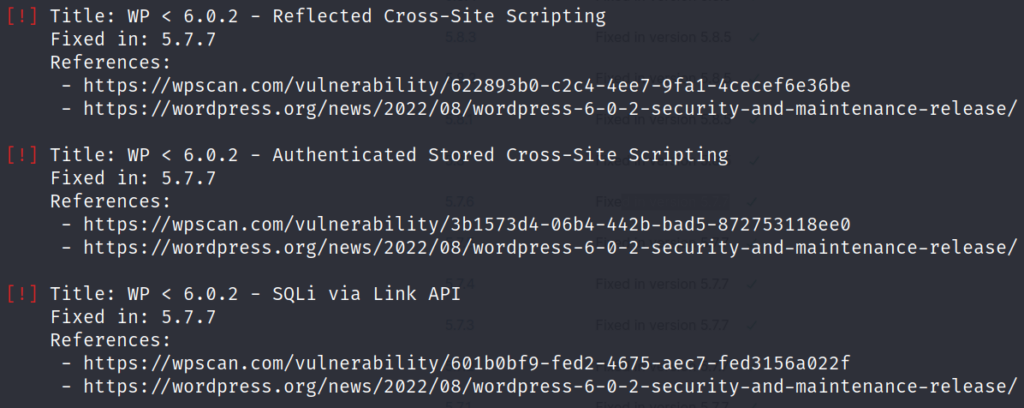
Further investigation on the malicious webshop
Furthermore, if you try to checkout and pay for an item on the website with PayPal you will be presented with a donate to person screen from PayPal:
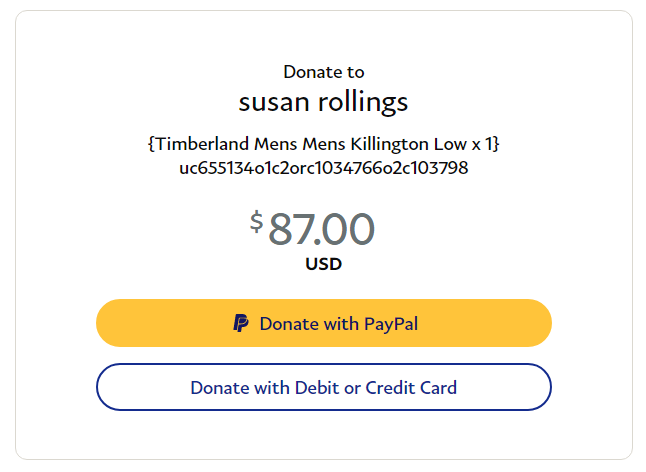
Online shops NEVER will use the donate or gift money feature in PayPal as this is used for sending money to friends or relatives or to charities, etc.
You have no buyer protection when using this feature and therefore is loved by these types of scammers.
When looking carefully at the URL the following can be observed:
https://www.paypal[.]com/donate/?cmd=_donations&item_number=uc655134o1c2orc1034766o2c103798&amount=87.00&business=laxzqaxuuubdhi@hotmail.com¤cy_code=USD&no_shipping=1&country=US&first_name=bogusdata&last_name=bogusdata&address1=bogusdata&address2=&city=bogusdata&state=bogusdata&zip=bogusdata&email=bogusdata&night_phone_b=¬ify_url=https://www.ytlyb.xyz/IPN/&item_name={Timberland%20Mens%20Mens%20Killington%20Low%20x%201}- The email used for this paypal account:
laxzqaxuuubdhi@hotmail[.]com(This looks like random generated email) - There is a notify_url specified:
notify_url=
https://www.ytlyb[.]xyz/IPN/&item_name={Timberland%20Mens%20Mens%20Killington%20Low%20x%201}This notify URL is the most interesting and is a feature from PayPal to setup your IPN listener with PayPal.
Instant Payment Notifications (IPNs) allow you to receive notifications whenever the state on an object changes (or something important happens to that object).
To set up IPNs for an object, set a callback_uri on that object. Whenever something important happens to the object that we think you should be notified of (typically a state change), we will make an HTTP POST request to your callback_uri with the object_id in the body of the request.
This URL is contacted when a payment goes through. This contacted domain doesn’t seem to be serving anything publicly and is registered at namesilo[.]com. The resulting IP is 209.74.107.226 which is part of Rebel Hosting who seem to host many other .xyz domains on their infrastructure.
Update 08-11-2022
No response and website is still compromised on publication day
The website still redirects to a web shop in similar style, but now under a different domain:
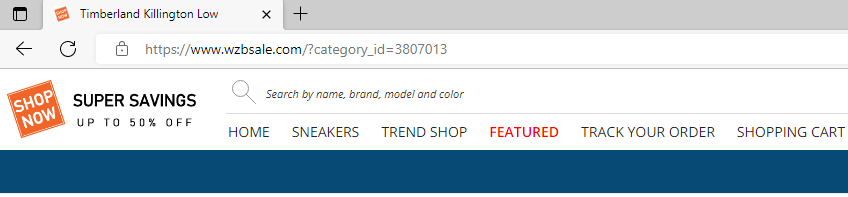
This domain has almost the same registrar information, it was only registered on a later date than the other domain.
As the 90 days have been surpassed, this blogpost will be published today!
Update 02-01-2023
Happy new year!
The website still redirects to a web shop in similar style, but now under a different domain:
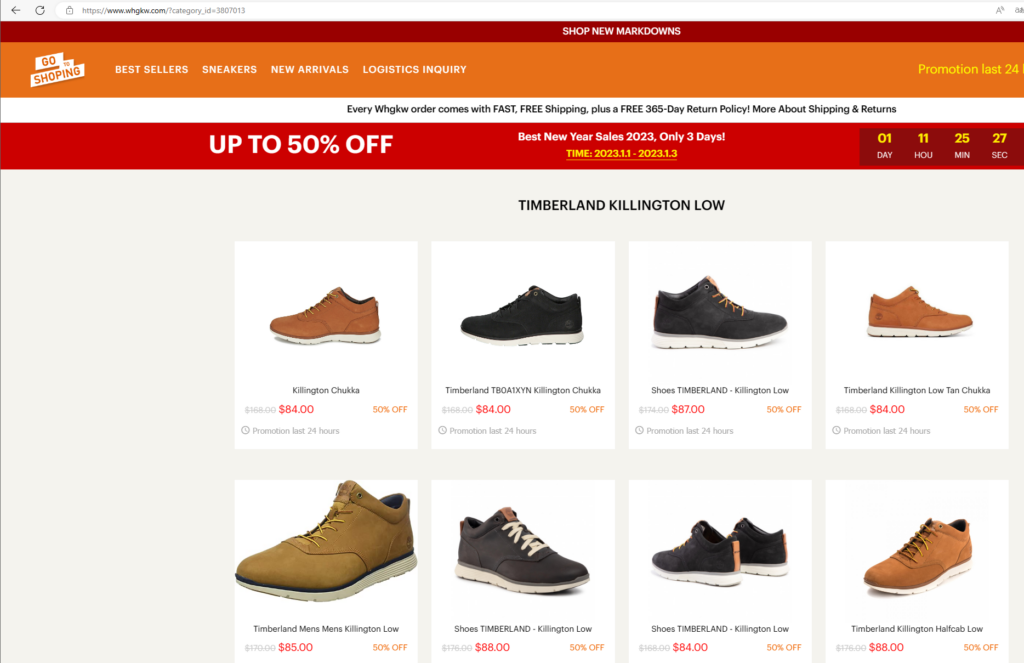
This domain has been registered at NameSilo with the registrar information replaced with PrivacyGuardian information.
What is PrivacyGuardian?
Purchasing domain names requires that certain data be made publicly available through a service called WHOIS. Furthermore, it is required that this information be kept up-to-date and accurate. Unfortunately, WHOIS has become a prime source for collecting personal information resulting in identity theft, SPAM and other unsolicited outreach.
We guard our customers by allowing their details to remain private while still complying with domain registration rules.
Closing remarks
I would again strongly recommend the webmaster to update WordPress, the affected plugins, and investigate why and how the site is redirecting users to a malicious domain.
Update 06-06-2023
The webmaster seems to have updated several plugins (not all) to fix the vulnerabilities they contained. It seems they also cleaned up the malicious code or plugin that caused the redirect because that isn’t working anymore.
I would still advice to keep the plugins and wordpress up to date more frequently.